The implementation strategy for Joint All Domain Command and Control (JADC2) lays out the pathway for future Joint Force networked command and control (C2). This complex planning effort offers an overarching framework to connect service efforts and to ensure that the United States can work effectively with its allies and partners. Centralized JADC2 guidance will be most useful to beat the drum for acquisition innovation, to drive interoperability among service programs and manage the seams between joint and service capabilities, to develop a management approach to ensure synchronization between existing and new elements as they are added in the future, to develop an experimentation agenda to reveal data sharing challenges to focus improvement efforts, and to serve as an entry point to C2 issues for partners and allies and to address issues of international data sharing. Along with these tasks, the JADC2 Cross Functional Team—or whatever ultimate central management function is instantiated—needs to focus on developing a common understanding and managing the architecture of the innovation ecosystem to achieve the Joint Force C2 vision.
The future of military command and control (C2) will be enabled by revolutions in information technology (IT). Step changes in computing power, almost unlimited cloud-enabled data storage, and advances in artificial intelligence (AI) and machine learning (ML) have opened up new opportunities for the Department of Defense (DoD) and the joint force. The capabilities enabled by this technological revolution have been a powerful motivator for new service-level programs working to enhance the capabilities available to military commanders. That said, the future fight demands that service capabilities work together seamlessly to ensure coherent multidomain warfighting strategies, meaning service-level C2 and targeting programs need to work together as a coherent whole. Joint All Domain Command and Control (JADC2) is the DoD’s concept to connect sensors and communications from all of the military services—Air Force, Army, Marine Corps, Navy, and Space Force—into a single network.1 As laid out in the JADC2 strategy, the goal is to ensure that the joint force commander has “the capabilities needed to command the Joint Force across all warfighting domains and throughout the electromagnetic spectrum to deter, and, if necessary, defeat any adversary at any time and in any place around the globe.”2
The Air Force’s Advanced Battle Management System (ABMS), the Navy’s Project Overmatch, and the Army’s Project Convergence are the three main efforts for advancing C2 at the service level. These programs seek cutting-edge targeting networks that match the right sensors to the right effectors to make forces more capable. Despite this unifying vision, these programs vary in approach, due to the different capabilities of each service. Project Convergence, the Army’s effort, focuses far more on exercises and experimentation as opposed to engineering enablers for existing capabilities.3 Project Overmatch and ABMS have a strong engineering emphasis with a focus on technology development, although there are fewer publicly available specifics on Project Overmatch.4
With all this activity, the question remains as to how to best ensure that progress toward enhanced C2 is not impeded by predictable challenges. The history of efforts on both service and joint IT-related programs suggests that the pathway to developing JADC2 is filled with potential risks and pitfalls. The problem set features rapid technological change, the necessity of interoperability with existing systems and with new systems across the services, integration with allies and partners, new and non-traditional contractors, and novel acquisition approaches.
This brief examines challenges in taking the next steps for enhanced C2 and targeting infrastructure and makes recommendations to help the U.S. military as it operates as a joint force and deploys with allies and partners. These recommendations are informed by the literature, by almost 20 non-attribution discussions with military and civilian experts from across the services (including current and retired personnel, up to the senior executive service (SES) civilian and general officer level) and defense contractors, and by participation at conferences and workshops, including one held at the Center for Strategic and International Studies. This work strove to identify strategic level challenges and relevant recommendations. In particular, the conversations with experts focused on enduring challenges that the interviewees did not think were being adequately addressed.
The research structured the discussions around four broad topics: (1) getting warfighters the C2 and targeting capabilities they need at the tactical edge, (2) integrating existing and new C2 technologies to support this goal, (3) management of the overall enterprise, and (4) the involvement of partners and allies. Asking these questions revealed challenges that, while difficult, the DoD has processes and procedures to address, such as the acquisition of complex technologies. It also revealed new concerns that will require both thoughtful recognition by leadership and creative solutions to address. Before examining each of these challenges in detail, this brief begins by exploring key observations about C2 and the implementation of JADC2.
C2 is a fractal challenge.
Effective C2 at the “tactical edge” in a contested environment shares similar challenges whether the frame of reference is within a service, at the joint level, or when working with allies and partners. Within services, there are challenges accessing, maintaining, transmitting, securing, and using the necessary data at the speed of the warfighter requirements. Additionally, sharing data across service components, for example across Naval aviation, surface ships, and submarines, requires thoughtful management. Ensuring an effective command structure is an enduring necessity. These challenges are replicated at the joint level as combatant commands (CCMDs) pull together service capabilities and prepare to fight. Finally, when the United States is working with partners and allies, the same challenges emerge again. This implies that effective C2 is a fractal challenge—any part of the enterprise has many of the same patterns and issues to address. This observation does not in and of itself yield solutions to any challenges, but it does mean that solutions to challenges that work at one level may be able to be repurposed and updated to help improve other levels.
JADC2 exists in an unusually complex ecosystem.
Any strategy aimed at developing a complex integrated capability must reflect an understanding of the equities, incentives, and constraints of the participants in the relevant ecosystems. The JADC2 strategy exists in a notably complex ecosystem driven by the military services as they engage in their Title 10 responsibilities to organize, train, and equip as other stakeholders in the national security apparatus are working to meet their own missions. The military services are not monolithic, and the incentives for operators and those for acquisition personnel are different, driving complexity. The C2 ecosystem includes the Joint Force itself, with combatant commanders making decisions and relying on effective connections across warfighting domains. The ecosystem includes the partners and allies alongside whom the United States may go to war. At all levels, warfighters need data, and the data must be shared with them and back to others. Other U.S. government agencies and the intelligence community set standards and provide actionable information. Finally, the ecosystem includes the contractors who provide the capabilities that support the JADC2 concept—and who are leading the innovation effort for some of these capabilities, which often have commercial roots. Other supporting and gap-filler capabilities, such as DARPA’s System-of-systems Technology Integration Tool Chain for Heterogeneous Electronic Systems (STITCHES) program, may rely on multiple DoD offices for funding as they scale.5 The complexity inherent in the JADC2 concept is not completely new, and past attempts at a network-centric systems faced many of these challenges. That history is associated with prominent failures, even when constrained to a single service, such as the Army’s Future Combat System.6 Those past programs offer caution for the JADC2 enterprise and support the approach of building up from service efforts and supporting and expanding on local successes rather than imposing and enforcing a top-down acquisition effort.
JADC2 faces a highly challenging problem set.
The expectation underpinning the JADC2 concept is that future conflict will be taking place in an environment that is contested in all domains by a highly capable state actor.7 This assumption fits with the vision laid out in the National Defense Strategy and the general consensus that the pacing threat for the U.S. military is a resurgent China.8 This strategic context guides any serious analysis of JADC2 toward the hardest problems in command, control, communications, computers, intelligence, surveillance, and reconnaissance (C4ISR): the denied, or at the very least contested environment.
The U.S. military has been effective at conducting C4ISR in permissive environments. Throughout operations in the Middle East since 9/11, the military has been able to control forces, share data, and cause kinetic effects. All of these capabilities have been possible in spite of a fractured C4ISR system, which the military has been able to use to support missions and effectively prosecute targets.9 The need for improved joint solutions such as JADC2 becomes necessary when planning for future conflicts in contested environments facing peer threats, which will necessitate rapid decision making and need to leverage data in new ways. Future conflict with a highly capable adversary, such as China, could be contested in all domains and take place across enormous operational theaters, all while the adversary has the advantage of operating near their borders. Nodes of the network may be attacked through cyber, electronic, or conventional means. A robust network should have multiple pathways for information, which means that connections with other services or with infrastructure managed by partner nations can be useful tools in building a more resilient network. If JADC2 is to add value to the capabilities of the joint force, its components must be able to function in that contested environment and manage significant distances between units, while taking advantage of the opportunities inherent in a networked concept. Understanding its operational environment is critical to understanding the context of the challenges faced by the JADC2 ecosystem.
Future conflict with a highly capable adversary, such as China, could be contested in all domains and take place across enormous operational theaters, all while the adversary has the advantage of operating near their borders.
Existing models may not be adequate for acquiring new capabilities.
Effective C2 is a not a new challenge but one that has endured throughout the history of warfighting as commanders have sought to communicate with distributed fighters and with one another. JADC2 represents the latest overarching effort to tie capabilities together effectively for the Joint Force. The unspoken but obvious implication here is that there will be some future effort aimed at solving the same challenge. Thus, JADC2 should not be understood as an endpoint or suite of capabilities with known end states but rather as several steps on the path toward greater interoperability across all domains in order to achieve joint effects.
Language from policymakers, including some in Congress, suggests that the vision for JADC2 is a definable finite set of capabilities that DOD is seeking to acquire. In the fiscal year 2023 defense authorization bill, the House Armed Services Committee included a requirement that the secretary of defense deliver a report inventorying “JADC2-related development efforts with descriptions of performance objects, costs and schedules and a list of potential JADC2 capability gaps along with how DoD plans to address and fund those gaps.”10 That language suggests that the capabilities are finite and that the JADC2 acquisition effort has a notional end date when all of those discrete enablers are acquired and integrated. This is how the military traditionally understands and designs acquisition programs, with program managers evaluated on cost, schedule, and performance. To get a new capability under this traditional process-focused model, the DoD develops a formal requirement, holds a competition, and buys a solution which it then operates and maintains until it is time for an upgraded or replacement capability. This generational approach ensures that capabilities are delivered and slowly updated, that program managers are working toward a destination, and that Congress is funding an end product.
Forcing JADC2 into that model is a mistake. Many of the technologies in the JADC2 family of systems are evolving on a rapid commercial timeline. Even the more traditional defense hardware-oriented aspects of JADC2 have software that will need to be regularly updated to retain connectivity and address adversary threats.11 Planning for some notional end-state when JADC2 is “done” and delivered suggests that there is a static goal for C2. Instead of a fixed goal, JADC2 should be thought of as a long-term journey of improvement to suites of interconnected capabilities. The steps along this journey will not all be incremental–developing data architectures and standards may require time-intensive consultative processes and significant investments. Even these larger leaps are not an end point, but instead will need to further evolve and be integrated into a wider set of systems. This insight has been reflected in the creation of a JADC2 cross-functional team approach which focuses on merging efforts through working groups rather than enacting acquisition on its own.12 The majority of JADC2-specific solutions connect service-acquired capabilities.13 JADC2 may include a relatively small set of joint capabilities tying together more robust service-procured capabilities.
Instead of a fixed goal, JADC2 should be thought of as a long-term journey of improvement to suites of interconnected capabilities.
Software development concepts like DevSecOps do incorporate an iterative approach where experience from operators feeds back into updates in a continuous flow, so the idea that IT-related capabilities need to be continually updated is not a new one. The DevSecOps approach could be a starting point for a JADC2 continuous development process, broadened out to include the interconnections between different families of capabilities.
One challenge is managing the inevitable seams between joint and service acquisition for capabilities designed for the joint force.
As currently envisioned, the JADC2 strategy ties together service C2 programs and thus includes both service-level and joint acquisition challenges. Each service program brings together multiple capabilities to create a coherent intraservice C2 system. Pulling service programs together for joint operations in support of the JADC2 concept requires an additional level of coordination to ensure that service programs can communicate with each other and operate together. These connections should also be managed over time—as subcomponents of the systems are updated, those joint connections must remain robust to ensure JADC2’s continued effectiveness.
There are alternative approaches to acquiring a joint capability, all of which have benefits and challenges.14 The expert discussions during this research revealed that these trade-offs remain a matter of concern, even as the DoD proceeds with service programs focused on joint operations.
Decentralized Development: The status quo approach involves each service developing its own C4ISR capabilities that could be tied together to meet the operational requirements of the JADC2 concept in a joint operation. In interviews, experts from a nontraditional defense contractor and a major prime contractor cited positive moves on data governance and standardization in recent months, but the overall inclination of first prioritizing intraservice connections remains. This is tempered by the role played by the JADC2 cross-functional team approach and other coordination goals laid out in the JADC2 strategy, as well as the attention paid to making data “visible, accessible, understandable, linked, trustworthy, interoperable, and secure” across the DoD, as outlined in the Five Data Decrees memo put forward by Deputy Secretary of Defense Hicks.15 Service led models would ensure that programs are designed to meet simpler, smaller goals, which could then be tied together—avoiding what one interviewee described as an operational vision “on the scale of solving world hunger”16—and achieve results at the speed of relevance. Service-level models also ensure clear operational focus and allow the services to balance priorities through the budgeting process.
Joint Development: Joint Program Executive Offices (JPEOs) could serve as a function to centralize management of JADC2 procurement and ensure data standardization, interoperability, a common approach to cybersecurity, and international coordination. The F-35 joint program office was offered, with some hesitation, as an example of a centralized organization generally with a focus on its functions rather than its acquisition outcomes, for example, as a place to locate foreign partner representatives. In public statements, Lieutenant General Dennis Crall, the director of the DoD’s J6, has argued for a degree of centralization but pushed back against the idea of a single JPEO taking on the management of the service programs.17 A JPEO may enhance interoperability but could result in services getting suboptimal solutions and also lead to delays due to increased coordination needs.18 Even with these flaws, for those dissatisfied with decentralized implementation, a JPEO was often the starting point when considering other options—and one interviewee offered that this model can help ensure accountability by offering a “forehead Congress can thump” should there be performance challenges such as interoperability failures.
Independent Agency: An independent agency could be used to acquire JADC2 capabilities and manage the enterprise. If the DoD decides to utilize a subordinate agency, it could either stand up a new agency or use an existing one such as the Defense Information Systems Agency (DISA) to manage procurement and be a touch point for international partners. This approach did not get much attention in the expert discussions. (Other research has identified uncertainty over what role DISA will play given that “JADC2 will fundamentally reshape DISA’s traditional mission and set the future path for its existing capabilities.”19)
Lead Military Service: The DoD could designate a lead service for JADC2 development and procurement. CCMDs, agencies, and the other services would be directed by the lead service and have to work to make sure that each service is meeting their requirements. The challenge is that service C2 needs are driven by different domains with distinct operational needs.
Lead CCMD: DoD could designate 1 of the 11 unified CCMDs, which are inherently joint and warfighter-focused, to lead the JADC2 effort. The DoD could designate a functional command, such as Cyber Command, or geographic combatant command, such as Indo-Pacific Command. Experts did not propose a single lead CCMD but repeatedly discussed the potential benefits of the CCMDs playing a larger role, given that geographic commands are a natural choice for identifying operators’ immediate needs in a region. That said, one expert cautioned that interoperability investments have not been high on CCMD priority lists in the past. Another, while not suggesting a particular structure, argued that the critical thing missing was achieving something “truly joint that’s attached to joint operational commanders.”20 That said, any joint approach will need to ensure that service-specific sensor to shooter kill chains are not made less effective in the search for commonality.
The fact that the structure of the acquisition organization came up in almost every interview suggests expert interest in ensuring that the acquisition strategy recognizes the risks inherent in a service-centered approach, even one with a coordination function as laid out in the JADC2 strategy document. Here and elsewhere, ensuring the joint warfighter perspective is captured in service-led acquisition is an abiding concern—and that is one of the important process contributions that a joint function can provide.
Given the concerns of experts, JADC2 acquisition should include the services doing a significant portion of the acquisition work and a joint function to ensure interoperability and to develop and manage an overarching technical architecture. Fortunately, services have been the traditional venue for acquisition, and so their challenges will be heavily focused on capturing new vendors and developing contract approaches for IT-driven systems. More challenging will be the joint component of the acquisition program. Currently the DoD Chief Information Officer and the J6 perform oversight of the JADC2 enterprise, and that has limited inherent problems from a process perspective. However, if this approach, or any centralized approach, begins to falter, there are several critical warning signs.
Here and elsewhere, ensuring the joint warfighter perspective is captured in service-led acquisition is an abiding concern—and that is one of the important process contributions that a joint function can provide.
A lack of operational interoperability, which will be evident through joint experimentation, exercises, or real-world responses to crises
A failure to make iterative progress on Services goals due to ambitious central goals that do not deliver near-term benefits
A lack of a single touch point for congressional oversight and accountability
A lack of a single touch point for partners and allies as they seek to integrate and understand U.S. systems
Constraints generated by the services that limit the use of data standards and open systems and interfaces even when technically viable
Limited or no common understanding of the threat picture and the most urgent challenges that need to be solved
A lack of meaningful joint testing and unclear evidence that the services are using the results of experimentation (although this is something of a lagging indicator since lessons from testing may come too late in program planning to generate change)
Along with ensuring that acquisition interests are balanced, the JADC2 ecosystem will need to manage these risks.
A key task will be ensuring innovation survives acquisition.
Technology development for DoD systems can be driven either by the DoD through the requirements and acquisition processes or by commercial industry as it works to develop products that will be successful in the relevant marketplace. In the aviation context, for example, fighter aircraft have no analogy in the commercial world in terms of performance requirements, so government investments have driven necessary innovations such as stealth.21 Engines for transport and tanker aircraft are often entirely or mostly commercial, and innovation is driven by the commercial market. The business model for airlines has led to reliability and efficiency improvements in these engines, which the DoD has benefited from.
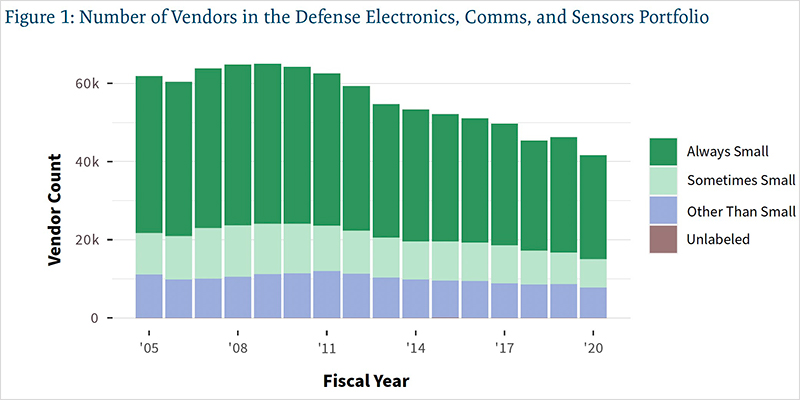
IT-driven military C2 programs may have originally been driven by the DoD’s needs, but over the last several decades, the expansion of commercial IT applications has meant that the DoD follows and benefits from IT development and innovation rather than leading it. Within the context of JADC2, the DoD will have to pursue development and procurement across both avenues while working on synchronizing its efforts with the pace of commercial innovation. Figure 1 shows the number of vendors supplying electronics, communications technologies, and sensors to the DoD and is based on Federal Procurement Data Systems (FPDS) information on government spending. CSIS’s analysis of the FPDS data reveals that there has been a steady decline in the total number of companies in this sector in the last 15 years, dropping by 37 percent. The absolute number of new entrants was higher 15 years ago and then declined along with the total number of vendors. It has more recently bumped up by over 300 vendors, returning to the pre-sequestration count—but as a percentage of the total vendors, new vendors have increased even more to 9.7 percent, a higher rate than other portfolios such as land vehicles, ships and submarines, or facilities and construction. If sustained, this higher rate of new entrants would be a sign that focused outreach to the commercial IT industry is beginning to produce industrial base dividends.
Some of the technologies enabling the JADC2 concept—those closest to the goal of more rapid closing of kill chains—will have no general commercial equivalent. The DoD will need to drive innovation for these as it has for many systems in the past. In others, such as data storage and data processing, the DoD will have to follow the lead of—and benefit from investments by—the commercial market to capture innovations at the speed of operation relevance. One commercial industry expert also raised a middle case—software-defined networks—where the DoD may need to rely on an approach developed outside the DoD that nonetheless has somewhat niche commercial market adoption but addresses key operational needs. While both ends of the spectrum have their own trade-offs and acquisition risks, a bigger challenge may be synchronizing commercial- and DoD-led capabilities into a coherent whole.
One challenge is that Silicon Valley’s products for commercial customers are not designed to be operated in a risky combat environment at the tactical edge; the DoD will need to drive solutions for low bandwidth-contested environments. When it comes to managing the acquisition of equipment for communication in a contested environment, the DoD is postured and has process tools to be able to acquire the capabilities the warfighter demands. What makes this segment of the JADC2 problem easier to navigate (if difficult to achieve because of the technical complexity of the components) is that it closely follows acquisition models set up by the DoD. The DoD generally has monopsony power (i.e., it is the only buyer) in the market for complex defense systems and has decades of experience working with its traditional contractor base to develop solutions for defense-specific problems. Communications platforms for contested environments fall well within that category because there is not significant civilian demand for jam-resistant communications systems, for example. While the DoD may be more accustomed to this problem, it should not close the door to outside innovation. Innovation in this communications problem could very well come from new vendors that are developing novel technologies such as laser-based communication systems.
One challenge is that Silicon Valley’s products for commercial customers are not designed to be operated in a risky combat environment at the tactical edge; the DoD will need to drive solutions for low bandwidth-contested environments.
The DoD has had a long history of struggling to capture commercial innovations. What makes JADC2 an especially difficult problem for acquisition officials is they will not be fielding a single, steady-state capability. Approaches to exploring include “as-a-service” acquisition and working with nontraditional vendors, along with expertise in managing multiple pathways in the Adaptive Acquisition Framework. For any of these approaches, new systems will have to employ open architectures that are tied to evolving JADC2 structure and standards and that are accessible to all qualified vendors.
As-a-service contracting is promising because of the speed of innovation in the private sector and how quickly technologies will have to be upgraded to stay on the cutting edge. Traditional government requirements set strict guidelines for suppliers and take place within an often slow acquisition process. If the DoD can embrace as-a-service contracting for components of JADC2 (likely non-denied cloud and AI/ML), then it will be better able to iterate technology at the speed of technological relevance and deliver capability to the warfighter at the speed of operational relevance. By building requirements around capabilities and not technical requirements, the DoD, along with a trusted contractor, can develop and deploy systems faster than would be possible with a traditional contracting approach. As service contracting combines well with software-defined systems to allow systems to keep pace with evolving C2 needs, although there could also be a hardware module update aspects to such arrangements.
A key component of capturing the technical innovation needed to make JADC2 work is bringing in technologies from outside the DoD’s traditional vendor ecosystem. The DoD has traditionally relied on a relatively small group of prime contractors that often specialize in the defense market. For technologies where the commercial market is driving innovation, including cloud computing and AI/ML, the DoD should engage outside of its traditional vendor base. Nontraditional companies have experience with cutting-edge technologies and expert workforces and thus may be positioned to adapt their technology to defense applications at the speed of relevance. The challenge is that nontraditional companies generally use capabilities like utilizing communications, networking, and cloud infrastructures that were not designed for use in an expeditionary or contested environment. The need thus is to identify where commercial companies currently offer technologies usable in contested environments, where they could with a reasonable amount of additional investment, and where it would be infeasible or not worthwhile for them to participate in the market.
Another challenge of bringing nontraditional contractors into the defense ecosystem is also not a new one and not limited to the JADC2 problem set. Part of the challenge is that the people and organizations responsible for the acquisition of JADC2-related capabilities acquisition are not the same people or organizations involved in acquisition process improvement efforts. Evolving acquisition approaches to facilitate acquisition of JADC2 capabilities may benefit from a direct connection between the two efforts, with acquisition streamlining and improvement efforts deliberately using JADC2 capabilities as the test case for change. By working on synchronizing the DoD’s efforts to the commercial ecosystem, the department may be able to develop technologies that maintain pace with the commercial world or at least reduce the current delay in fielding cutting-edge technologies.
JADC2 will require an approach to testing and experimentation that links to its structure as an evolving set of interoperable systems (which again will require open architectures and increasing use of software-defined capabilities). Aiming at a point where development or testing is “complete” will mean that the framework for the program does not include the consistent onboarding of new capabilities. Testing will need to be an ongoing part of the program rather than a step to complete along the way, of which testing interoperability of service-based systems as they evolve is a significant driver. The sheer scale and complexity of the systems will further complicate testing. While live testing is necessary to unpack challenges, a JADC2-focused virtual test environment would facilitate more continuous testing.
Along with improving coordination inside DoD, effective employment of JADC2 in the future fight will require bridging the gap with allies.
The importance of working with allies and partners was stressed in nearly every one of the expert discussions. That the United States will not fight alone in the future is a truism, and JADC2 is in part designed to facilitate integration with allies and partners, although there are still many areas needing further definition.22 Furthermore, there is evidence that JADC2 programs are engaged in developing the necessary relationships now to ensure that they will be practiced in case of a future fight. The Army’s 2022 Project Convergence exercises, for example, were designed to include international partners.23
In spite of these and other efforts underway, interviewees frequently raised the concern that many aspects of this cooperation have not been worked out. Specifically, while this coordination challenge is well known, efforts to resolve it have not gotten to the level of detail necessary to develop confidence in the exchange of critical information in advance of a fight. In particular, C2 cooperation with allies was highlighted as making interoperability more difficult to achieve. Part of the challenge is the profusion and heterogeneity of systems both within the United States at various levels of classification and across U.S. partners. Multiple experts raised the concern that the capability for handling classified materials has to be baked in from the start; iteration from an open system does not have a straightforward path for evolution to handle higher levels of classification later. That said, this can be solved through the acquisition of systems that can be accessed by multiple partners at different levels of classification—so this is a problem that has an acquisition solution, no matter how complicated that solution may be in practice.
A larger challenge comes from what will actually happen during a fight. In every contingency, the force generating the data will need to determine what information it does and does not want to share with its allies (and they will naturally do the same). Furthermore, the levels of data sharing and information access may vary over the course of the battle. Some questions to address include: What are the triggers for data sharing? What might trigger data sharing at different levels of classification? Who is responsible for identifying when allies and partners need more data, and who is in charge of getting it to them? What kinds of technology and infrastructure need to be in place in advance of the fight to facilitate data sharing? These are the kinds of questions that interviewees were more concerned about than the specifics of the networks over which information will be shared.
The answers to these questions will likely differ in every engagement, but none of the interviewees raised technical challenges as the main concern. Rather, they were focused on the process for identifying key questions and the approach for developing answers—and recommended doing this in advance. Allied defense organizations may often be willing to scale up data sharing in a crisis, but without advanced preparations, willingness will not translate into effective coordination. One strong recommendation throughout the interviews and in the literature was to not wait until any future engagement starts to begin the process of integrating partners and practicing the information exchange. Experimentation can help identify the political barriers to working with other nations. One interviewee suggested the necessity of working with allies and partners begins with setting requirements and highlighted the preferability of doing so from the beginning rather than in retrospect.
Allied defense organizations may often be willing to scale up data sharing in a crisis, but without advanced preparations, willingness will not translate into effective coordination.
Along with following the Five Data Decrees, additional solutions to the challenge of working with partners include open interfaces so that a variety of systems can plug into a common backbone and exchange information. A second is involving the contractor base in experiments to allow for early insight into data-sharing sticking points and evolve requirements along the way. Regardless of the approach, it is clear that experimentation and exercising with allies is critical if JADC2 is to be interoperable with allies and partners. The future is uncertain, and even if experiments are wrong, specific lessons drawn from exercises will help with understanding what decisions need to be made and how to communicate.
One theme resonated throughout the expert interviews. Rather than focus on JADC2 as a distinct set of capabilities and enablers and as an endpoint to a set of acquisition programs, it should be understood as a guidepost for an effort across the defense enterprise to advance C4ISR capabilities to meet the challenges of future conflict against a peer adversary. Understanding JADC2 as a process will help the DoD focus on innovation instead of acquisition. The mission, the threat landscape, and perhaps even the pacing threat will change over time, and the technology will need to change and evolve in parallel. The very nature of C2, with its interconnected set of capabilities, advocates for an open-system approach where new innovations can seamlessly plug into existing architectures. This framework for understanding JADC2 will enable the DoD to take more incremental steps to improving its capabilities, including C4ISR, as opposed to attempting to take a generational leap. This will almost certainly help control costs while driving up fielded performance. Some aspects of this problem, such as developing a successor to the Link 16 architectures, evolving data standards, or providing a joint commercial cloud, may benefit from more centralized approaches, but these mission sets should be tightly defined and take on no more complexity than necessary. This requires the recognition that aspects of the programs that rely on interconnected software, especially commercial derivative technology, may never be “complete” in the sense of a static delivered capability. The DoD should treat the JADC2 concept as a guiding North Star for managing innovation rather than as a set of procurement programs with a final delivery endpoint.
Measuring progress toward the JADC2 vision will be difficult in an environment where the requirements and capabilities for these technologies are constantly evolving. The DoD will likely never be able to meet the goal of connecting every sensor with every effector, especially on a battlefield becoming increasingly sensor saturated and complex. That does not mean the DoD should simply surrender. Instead, the DoD should develop meaningful metrics and goals for improvement towards the goal of the technology. Measuring progress toward meaningful goals will be difficult in a space where the goal posts themselves will continue to change, but doing so could help secure funding, attention, and results for the enterprise.
Another tension to consider is that attempting revolutionary change can reduce attention to current problems. Generational changes like JADC2 tend to focus on time and resource-intensive steps with the potential for enormous payoffs in the longer term—but at the potential expense of putting off important challenges that could be addressed in the near term but have characteristics that the present system is not incentivized to address. For C2, the acquisition system is making slow but steady progress on intraservice capabilities but lags on progress on joint and international cooperation. Waiting until JADC2 capabilities are delivered to address these current challenges could mean that solutions are not adequately incorporated during development, and that gaps remain in the near term.
Understanding the challenges and opportunities for JADC2 are necessary but not sufficient to address the thorny problems inherent in such a complex effort. The JADC2 CFT—as the organization assigned by DoD leadership to execute the JADC2 strategy (or whatever ultimate central management function is instantiated)—needs to go beyond the management of “the plans of actions, milestones, and resourcing requirements” toward the development of a common understanding and management of the architecture of the innovation ecosystem to achieve the Joint Force C2 vision.24
Cynthia Cook is director of the Defense-Industrial Initiatives Group and a senior fellow in the International Security Program at the Center for Strategic and International Studies (CSIS) in Washington, D.C. Rose Butchart is an associate fellow with the Defense-Industrial Initiatives Group at CSIS. Alexander Holderness is a former research assistant with the Defense-Industrial Initiatives Group at CSIS. Gregory Sanders is deputy director and fellow with the Defense-Industrial Initiatives Group at CSIS.
评论